A Distributed Denial of Service (DDoS) attack is a malicious attempt to make an online service, website, or network resource unavailable to users by overwhelming it with a flood of illegitimate requests. Unlike traditional Denial of Service (DoS) attacks that are launched from a single source, DDoS attacks involve multiple sources, making them more powerful and difficult to mitigate.
How Does a DDoS Attack Work?
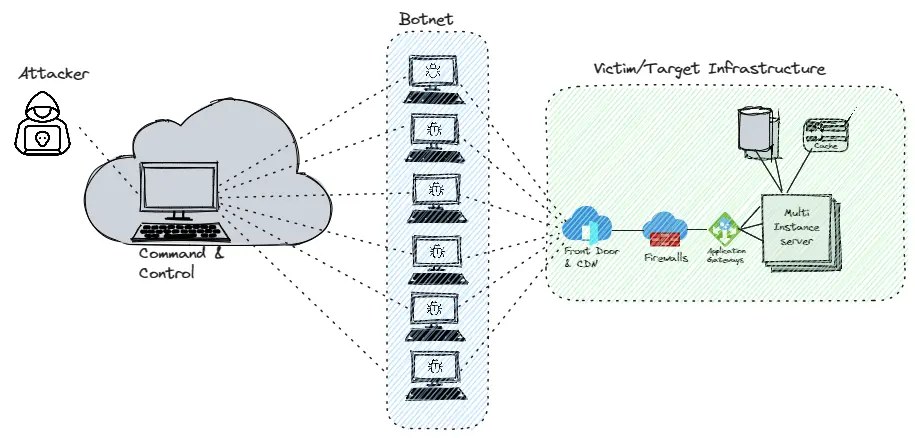
DDoS attacks typically carried out from a network of compromised (infected with malware) computers, known as a botnet, to send a massive volume of traffic to the target simultaneously. Attackers controls each bot remotely to send requests to target’s IP addresses.
As the flooding doesn’t happens from single device, segregating the attack traffic is difficult.
What are different types of DDoS Attacks?
Here are some of the common DDoS attacks at different layers of OSI model.

Read What is the OSI model? Real life example with file sharing
- Application layer:
- HTTP flood: Target web servers flooded with HTTP requests; resources exhausted very quickly leading to service unavailability.
- Slowloris: Attackers sends incomplete requests and keep them open, server resources get tied up and causing finally denial of service.
- Transport layer:
- SYN flood: Flood off TCP SYN packets were sent to the target server and eventually exhausting the target resources by keeping the connections open.
- UDP flood: Targets were flooded with high volume of User Datagram Protocol (UDP) packets. Network infrastructure or the services that rely on the UDP get disrupted.
- Network layer:
- ICMP flood: Attackers flood the target with large number of Internet Control Message Protocol (ICMP) packets as a result network gets congested and unavailable eventually.
- Smurf Attack: Attackers send ICMP pings to network broadcast addresses, causing multiple hosts to reply simultaneously and overwhelming the target’s network resources.
- Data link layer:
- MAC flood: Attackers floods network switch with large no of MAC addresses. Switch’s Mac forward table gets full leading to network congestion and denial of services.
DDoS attack can happen at multiple layers which makes it very difficult to mitigate sometimes also attackers may employ various combinations of attack techniques to achieve their goals.
How to mitigate DDoS Attack?
Preventing and mitigating DDoS attacks require a multi-layered defense approach, including network monitoring, traffic analysis, rate limiting and collaboration with DDoS mitigation service providers.
There are several market-available tools and services designed to protect against DDoS attacks. some of the widely recognized and effective options:
- Content Delivery Networks (CDNs):
- Akamai: Akamai provides DDoS protection services that leverage their extensive global network infrastructure to absorb and mitigate large-scale attacks.
- Cloudflare: Cloudflare offers DDoS protection through their CDN, providing advanced traffic filtering, rate limiting, and DNS protection services.
- DDoS Mitigation Service Providers:
- Arbor Networks: Arbor Networks offers a range of DDoS protection solutions, including on-premises hardware appliances and cloud-based services for effective attack detection and mitigation.
- Radware: Radware provides both on-premises and cloud-based DDoS protection solutions, utilizing behavioral analysis and machine learning algorithms for real-time threat detection and mitigation.
- Network Security and Traffic Analysis:
- Cisco ASA (Adaptive Security Appliance): Cisco ASA offers robust firewall capabilities, intrusion prevention systems (IPS), and advanced threat detection to defend against DDoS attacks.
- F5 Networks: F5 Networks provides traffic analysis tools, including their BIG-IP platform with advanced DDoS protection features, such as rate limiting, traffic steering, and behavioral analytics.
- Cloud-Based DDoS Protection Services:
- Amazon Web Services (AWS) Shield: AWS Shield offers scalable DDoS protection for applications running on the Amazon Web Services platform, providing automatic detection and mitigation of attacks.
- Microsoft Azure DDoS Protection: Azure DDoS Protection is a cloud-based service that safeguards applications and services hosted on the Azure platform, utilizing traffic monitoring, anomaly detection, and mitigation capabilities.
Read SaaS vs. PaaS vs. IaaS Which Cloud Service model to choose
It’s important to note that choosing the right tool or service depends on the specific needs and requirements of your organization. Consider factors such as the scale of your infrastructure, budget, and desired level of protection when evaluating and selecting a DDoS protection solution. Additionally, working with experienced security professionals or consulting firms can provide valuable insights and guidance in choosing the most suitable solution for your environment.
Takeaway 💡
Did you include rate-liming in DDoS mitigation strategy? Where will you implement this, in application’s code, CDN, API gateway or firewall.


Good write-up, I am normal visitor of one抯 website, maintain up the excellent operate, and It is going to be a regular visitor for a lengthy time.